Sidebar
Table of Contents
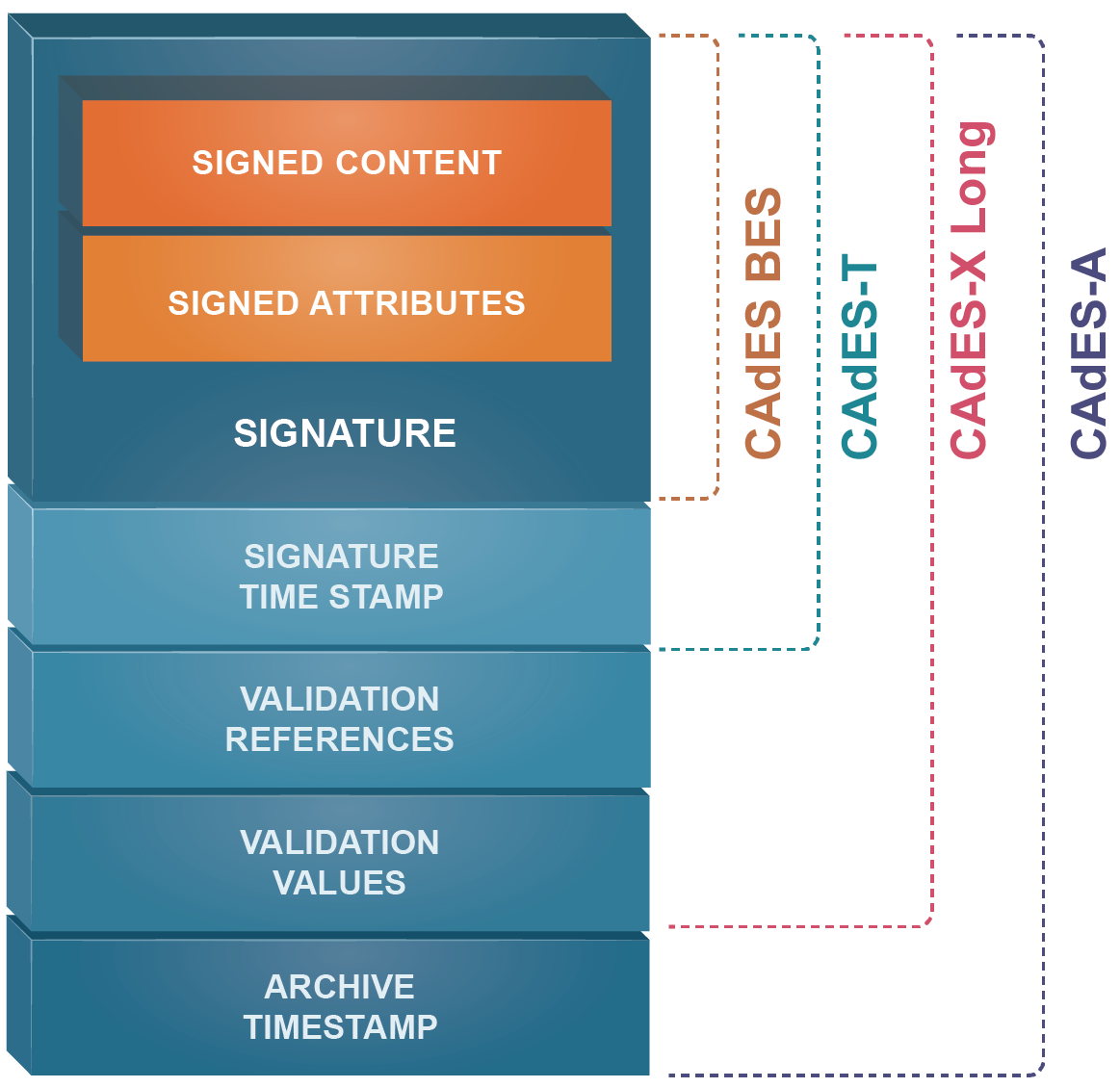
CAdES-A
General Information
ES-A (Archival Electronic Signature) is the signature format that should be used in cases where signed documents need to be stored longer than the validity period of the certificate authority's root/sub-root, OCSP and timestamp certificates.
Archiving is done when the CA’s certificate is near to the end of the validity period or the certificates are revoked or if announced that the used algorithms become invalid or is changed. There is no inconvenience in making archival before the above situations occur. Archival should be repeated by entering timestamp settings published by a new hierarchy by TSP if the validity of the last archive timestamp in the currently signed archive documents is compromised. On the application side, the relevant infrastructure should be provided.
The following table specifies the signature properties that must be included in the signature file for CAdES-A signature format:
| Signature Properties | CADES-A | |
|---|---|---|
| Signed Attributes | Content-type | M |
| Message-digest | M | |
| ESS signing-certificate v2 | M | |
| Signing-time | O | |
| Content-hints | O | |
| Mime-type | M | |
| Content-reference | O | |
| Content-identifier | O | |
| Commitment-type-indication | O | |
| Signer-location | O | |
| Content-time-stamp | O | |
| Signature-policy-identifier | O | |
| Unsigned Attributes | CounterSignature | O |
| Signature-time-stamp | M | |
| Complete-certificate-references | M | |
| Complete-revocation-references | M | |
| Certificate-values | M | |
| Revocation-values | M | |
| CAdES-C-time-stamp | E | |
| CAdES-C-time-stamped-certs-crls-references | E | |
| Archive-time-stamp | M |
M: Must - It is mandatory to provide the specified substance. If the substance is not provided, the e-signature conformity assessment will result in a negative.
O: It is optional to provide the specified substance. If the substance is not provided, the e-signature conformity assessment will not result in a negative.
E: One of the elective options on the same column can be selected optionally.
The timestamp received from the user's system clock or the owner of the signature application does not guarantee the accuracy of the signature time because it is not signed by a trusted server. For this reason, it is not recommended to use the signing time attribute. If it is used, it must be adjusted so that it is left behind from the timestamp.
Procedure
You can access CAdES-A Detached Test Package from here.
You can access CAdES-A Attached Test Package from here.
You can access test root certificates from here.
The following table provides the names and properties of the signature files to be used in the procedures:
| M/O | Signed Document Name | Signed Document Property | Validation Result | Explanation |
|---|---|---|---|---|
| M | ESA_1 | Valid (Revocation check is available only via CRL and all signed attributes are added) | VALID | All signed attributes must be displayed in the validation result |
| O | ESA_2.doc | Signature file with a macro inserted content | INVALID | The signature should not be verified |
| M | ESA_3 | Contradictory signature file including “mime-type” attribute with “image/jpeg” value although the actual content type is “Application/pdf” | INVALID | Signature verification details must be shown. |
| M | ESA_4 | Signature file with a forged “ESS Signing-Certificate-v2” attribute | INVALID | Signature verification details must be shown. |
| M | ESA_5 | Signature file with a forged ”message-digest” attribute | INVALID | Signature verification details must be shown. |
| M | ESA_6 | Signature file in which SHA-1 digest algorithm is used | VALID | The signature must be archived. |
| M | ESA_7 | Signature file with a forged signature | INVALID | Signature verification details must be shown. |
| M | ESA_8 | Valid (Revocation check is available only via OCSP) | VALID | |
| M | ESA_9 | Signature file signed by a certificate with an omitted “non-repudiation” field in the key usage extension | INVALID | Signature verification details must be shown. |
| M | ESA_10 | Signer certificate with an omitted “UserNotice” text field in the “CertificatePolicies” extension | INVALID | Signature verification details must be shown. |
| M | ESA_11 | Signer certificate with an omitted ETSI OID in “QualifiedCertificateStatements” extension | INVALID | Signature verification details must be shown. |
| M | ESA_12 | Signer certificate with an omitted ICTA OID in “QualifiedCertificateStatements” extension | INVALID | Signature verification details must be shown. |
| O | ESA_13 | Signature file which has a PDF/A-3 content with attachment | INVALID | The signature must not be verified. |
| M | ESA_14 | Signer certificate has expired before signature timestamp | INVALID | Signature verification details must be shown. |
| M | ESA_15 | Signer certificate has a forged signature | INVALID | Signature verification details must be shown. |
| M | ESA_16_1 | Signature file signed by a revoked certificate before signature timestamp (Revocation check is available only via CRL) | INVALID | Signature verification details must be shown. |
| M | ESA_16_2 | Signer certificate has revoked after signature timestamp (Revocation check is available only via CRL) | VALID | |
| M | ESA_17_1 | Signer certificate has revoked before signature timestamp (Revocation check is available only via OCSP) | INVALID | Signature verification details must be shown. |
| M | ESA_17_2 | Signer certificate revoked in OCSP after signature timestamp (Revocation check is available only via OCSP) | VALID | |
| M | ESA_18 | The validity of signer certificate has to be checked via an expired CRL | INVALID | Signature verification details must be shown. |
| M | ESA_19 | The validity of signer certificate has to be checked via a signature forged CRL | INVALID | Signature verification details must be shown. |
| M | ESA_20 | The validity of signer certificate has to be checked via an expired OCSP response | INVALID | Signature verification details must be shown. |
| M | ESA_21 | The validity of signer certificate has to be checked via an OCSP response having forged signature | INVALID | Signature verification details must be shown. |
| M | ESA_22 | The validity of signer certificate has to be checked via an OCSP response which is signed by an expired OCSP certificate | INVALID | Signature verification details must be shown. |
| M | ESA_23 | The validity of signer certificate has to be checked via an OCSP response which is signed by a signature forged OCSP certificate | INVALID | Signature verification details must be shown. |
| M | ESA_24_1 | The validity of signer certificate has to be checked via an OCSP response which is signed by a revoked OCSP certificate. The OCSP certificate is revoked before signature timestamp | INVALID | Signature verification details must be shown. |
| M | ESA_24_2 | The validity of signer certificate has to be checked via an OCSP response which is signed by a revoked OCSP certificate. The OCSP certificate is revoked after signature timestamp | VALID | |
| M | ESA_25 | Signer certificate has a monetary limit which is equal to “0” | CHOICE* | |
| O | ESA_26 | Signer certificate has a usage restriction defined in “QC Statements” extension | INVALID | The signature should not be verified. |
| M | ESA_27 | The validity of signer certificate has to be checked via an OCSP response which is generated for a different certificate | INVALID | Signature verification details must be shown. |
| M | ESA_28 | Signer certificate is issued by an intermediate CA certificate having a forged signature | INVALID | Signature verification details must be shown. |
| M | ESA_29_1 | Signer certificate is issued by an intermediate CA certificate which is revoked in CRL before signature timestamp | INVALID | Signature verification details must be shown. |
| M | ESA_29_2 | Signer certificate is issued by an intermediate CA certificate which is revoked in CRL after signature timestamp | VALID | |
| M | ESA_30 | Signer certificate is issued by an intermediate CA certificate whose validity has to be checked via an expired CRL | INVALID | Signature verification details must be shown. |
| M | ESA_31 | Signer certificate is issued by an intermediate CA certificate whose validity has to be checked via a forged signature CRL | INVALID | Signature verification details must be shown. |
| M | ESA_32_1 | Signer certificate is issued by an intermediate CA certificate which is revoked in OCSP before signature timestamp | INVALID | Signature verification details must be shown. |
| M | ESA_32_2 | Signer certificate is issued by an intermediate CA certificate which is revoked in OCSP after signature timestamp | VALID | |
| M | ESA_33 | Signer certificate is issued by an intermediate CA certificate whose validity has to be checked via an expired OCSP response | INVALID | Signature verification details must be shown. |
| M | ESA_34 | The validity of intermediate CA certificate has to be checked via an OCSP response which has a forged signature | INVALID | Signature verification details must be shown. |
| M | ESA_35 | The validity of intermediate CA certificate has to be checked via an OCSP response which is signed by an expired OCSP certificate | INVALID | Signature verification details must be shown. |
| M | ESA_36 | The validity of intermediate CA certificate has to be checked via an OCSP response which is signed by a signature forged OCSP certificate | INVALID | Signature verification details must be shown. |
| M | ESA_37_1 | The validity of intermediate CA certificate has to be checked via an OCSP response which is signed by a revoked OCSP certificate. The OCSP certificate is revoked before signature timestamp | INVALID | Signature verification details must be shown. |
| M | ESA_37_2 | The validity of intermediate CA certificate has to be checked via an OCSP response which is signed by a revoked OCSP certificate. The OCSP certificate is revoked after signature timestamp | VALID | |
| M | ESA_38 | The root certificate has a forged signature | INVALID | Signature verification details must be shown. |
| M | ESA_39_s | Counter signature file signed by two signers. Second signer has a valid certificate, but the first signer is configured with the required intermediate CA certificate which is revoked | INVALID | Validation result of the each signer must be shown in a hierarchical order similar to the tree structure. Signature verification details must be shown. |
| M | ESA_39_p | Parallel signature file signed by two signers. Second signer has a valid certificate, but the first signer is configured with the required intermediate CA certificate which is revoked | INVALID | Each signature validation result must be shown in a hierarchical order similar to the tree structure. The details of the error should be reported to the user |
| M | ESA_40 | Signature timestamp has a “TSTInfo” with a forged “messageImprint” field (TS server is TSA1) | INVALID | Signature verification details must be shown |
| M | ESA_41 | Signature timestamp has a forged signature (TS server is TSA2) | INVALID | Signature verification details must be shown. |
| M | ESA_42 | Signature timestamp is signed by an expired certificate (TS server is TSA3) | INVALID | Signature verification details must be shown |
| M | ESA_43 | Signature timestamp is signed by a certificate with a forged signature (TS server is TSA4) | INVALID | Signature verification details must be shown |
| M | ESA_44 | Signature timestamp is signed by a revoked certificate. The TS certificate is revoked before signature timestamp (TS server is TSA5) | INVALID | Signature verification details must be shown |
| M | ESA_45 | Signature timestamp is signed by a revoked certificate.The TS certificate is revoked after signature timestamp (TS server is TSA5) | VALID | |
| M | ESA_46 | Signature timestamp is signed by a certificate whose issuer certificate is forged (TS server is TSB) | INVALID | Signature verification details must be shown. |
| M | ESA_47 | Signature timestamp is signed by a valid certificate (TS Server is TSC1) | VALID | |
| M | ESA_48 | Signature timestamp is signed by a certificate which references an expired CRL (TS server is TSC2) | INVALID | Signature verification details must be shown. |
| M | ESA_49 | Signature timestamp is signed by a certificate which references a CRL with a forged signature (TS server is TSC3) | INVALID | Signature verification details must be shown. |
| M | ESA_50 | Signature file with a “Complete certificate references” attribute which does not have a root certificate reference | INVALID | Signature verification details must be shown. |
| M | ESA_51 | Signature file with a “Complete certificate references” attribute which has a wrong root certificate reference | INVALID | Signature verification details must be shown. |
| M | ESA_52 | Signature file with a “Complete certificate references” attribute which does not have an intermediate CA certificate reference | INVALID | Signature verification details must be shown. |
| M | ESA_53 | Signature file with a “Complete certificate references” attribute which has a wrong intermediate CA certificate reference | INVALID | Signature verification details must be shown. |
| M | ESA_54 | Signature file with a “Complete revocation references” attribute which does not have a CRL reference for intermediate CA | INVALID | Signature verification details must be shown. |
| M | ESA_55 | Signature file with a “Complete revocation references” attribute which has a wrong CRL reference for intermediate CA | INVALID | Signature verification details must be shown. |
| M | ESA_56 | Signature file with a “Complete revocation references” attribute which does not have a CRL reference for signer certificate | INVALID | Signature verification details must be shown. |
| M | ESA_57 | Signature file with a “Complete revocation references” attribute which has a wrong CRL reference for signer certificate | INVALID | Signature verification details must be shown. |
| M | ESA_58 | Signature file with a “Complete revocation references” attribute which does not have an OCSP Reference for intermediate CA | INVALID | Signature verification details must be shown. |
| M | ESA_59 | Signature file with a “Complete revocation references” attribute which has a wrong OCSP Reference for intermediate CA | INVALID | Signature verification details must be shown. |
| M | ESA_60 | Signature file with a “Complete revocation references” attribute which does not have an OCSP reference for signer certificate | INVALID | Signature verification details must be shown. |
| M | ESA_61 | Signature file with a “Complete revocation references” attribute which has a wrong OCSP reference for signer certificate | INVALID | Signature verification details must be shown. |
| M | ESA_62_1 | “sigAndRefTimeStamp” has a “TSTInfo” with a forged “messageImprint” field (TS server is TSA1) | INVALID | Signature verification details must be shown. |
| M | ESA_63_1 | “sigAndRefTimeStamp” has a forged signature (TS server is TSA2) | INVALID | Signature verification details must be shown. |
| M | ESA_64_1 | “sigAndRefTimeStamp” is signed by an expired certificate (TS server is TSA3) | INVALID | Signature verification details must be shown. |
| M | ESA_65_1 | “sigAndRefTimeStamp” is signed by a certificate with a forged signature (TS server is TSA4) | INVALID | Signature verification details must be shown. |
| M | ESA_66_1 | “sigAndRefTimeStamp” is signed by a revoked certificate. The revocation time is before the signing time (TS server is TSA5) | INVALID | Signature verification details must be shown. |
| M | ESA_67_1 | “sigAndRefTimeStamp” is signed by a revoked certificate. The revocation time is after the signature timestamp (TS server is TSA5) | VALID | |
| M | ESA_68_1 | “sigAndRefTimeStamp” is signed by a certificate whose issuer certificate is forged (TS server is TSB) | INVALID | Signature verification details must be shown. |
| M | ESA_69_1 | “sigAndRefTimeStamp” is signed by a valid certificate (TS Server is TSC1) | VALID | |
| M | ESA_70_1 | “sigAndRefTimeStamp” is signed by a certificate which references an expired CRL (TS server is TSC2) | INVALID | Signature verification details must be shown. |
| M | ESA_71_1 | “sigAndRefTimeStamp” is signed by a certificate which references a CRL with a forged signature (TS server is TSC3) | INVALID | Signature verification details must be shown. |
| M | ESA_72 | Signature file with a ”Certificate Values” attribute which does not have a root certificate value | INVALID | Signature verification details must be shown. |
| M | ESA_74 | Signature file with a ”Certificate Values” attribute which does not have an intermediate CA certificate value | INVALID | Signature verification details must be shown. |
| M | ESA_76 | Signature file with a ”Revocation Values” attribute which does not have a CRL value for intermediate CA certificate | INVALID | Signature verification details must be shown. |
| M | ESA_78 | Signature file with a ”Revocation values” attribute which does not have a CRL for signer certificate | INVALID | Signature verification details must be shown. |
| M | ESA_80 | Signature file with a ”Revocation values” attribute which does not have an OCSP value for intermediate CA certificate | INVALID | Signature verification details must be shown. |
| M | ESA_82 | Signature file with ”Revocation values” attribute which does not have an OCSP value for signer certificate | INVALID | Signature verification details must be shown. |
| M | ESA_84 | “archiveTimeStamp” has a “TSTInfo” with a forged “messageImprint” field (TS server is TSA1) | INVALID | Signature verification details must be shown. |
| M | ESA_85 | “archiveTimeStamp” has a forged signature (TS server is TSA2) | INVALID | Signature verification details must be shown. |
| M | ESA_86 | “archiveTimeStamp” is signed by an expired certificate (TS server is TSA3) | INVALID | Signature verification details must be shown. |
| M | ESA_87 | “archiveTimeStamp” is signed by a forged certificate (TS server is TSA4) | INVALID | Signature verification details must be shown. |
| M | ESA_88 | “archiveTimeStamp” is signed by a revoked certificate. The revocation time is before the signing time (TS server is TSA5) | INVALID | Signature verification details must be shown. |
| M | ESA_89 | “archiveTimeStamp” is signed by a revoked certificate. The revocation time is after the signature timestamp (TS server is TSA5) | VALID | |
| M | ESA_90 | “archiveTimeStamp” is signed by a certificate whose issuer certificate is forged (TS server is TSB) | INVALID | Signature verification details must be shown. |
| M | ESA_91 | “archiveTimeStamp” is signed by a valid certificate (TS Server is TSC1) | VALID | |
| M | ESA_92 | “archiveTimeStamp” is signed by a certificate which references an expired CRL (TS server is TSC2) | INVALID | Signature verification details must be shown. |
| M | ESA_93 | “archiveTimeStamp” is signed by a certificate which references a CRL with a forged signature (TS server is TSC3) | INVALID | Signature verification details must be shown. |
| O | ESA_94 | “signatureTimeStamp” root certificate is not added to the signature file (TS server TSC1) | INVALID | The signature should not be verified. |
| M | ESA_95 | “signatureTimeStamp” CRL is not added to the signature file (TS server TSC1) | INVALID | Signature verification details must be shown. |
| O | ESA_96 | “sigAndRefTimeStamp” root certificate is not added to the signature file (TS server TSC1) | INVALID | The Signature should not be verified. |
| M | ESA_97 | “sigAndRefTimeStamp” CRL is not added to the signature file (TS server TSC1) | INVALID | Signature verification details must be shown. |
| O | ESA_100 | Signature file has two “archiveTimeStamp”. First one's root certificate is not added to the signature file (TS server TSC1) | INVALID | The signature should not be verified. |
| M | ESA_101 | Signature file has two “archiveTimeStamp”. First one's CRL is not added to the signature file (TS server TSC1) | INVALID | Signature verification details must be shown. |
| M | ESA_106 | “archiveTimeStamp” certificate is expired after the signature timestamp | VALID | The signature must be archived. |
| M | ESA_109 | “archiveTimeStamp” with SHA-1 digest algorithm | VALID | The signature must be archived. |
| O | ESA_110 | Signature file without a “mime-type” attribute | INVALID | The signature should not be verified. |
* One of the following methods must be selected when verifying the signed document if the signer certificate includes a monetary limit:
- “INVALID Signature” message must be displayed. The description of the error should be reported to the user.
- The monetary limit of the certificate is compared with the monetary limit of the signed document and if the monetary limit of the certificate is sufficient for the monetary value of the signed document, “VALID Signature” message must be displayed.
- In the case where the monetary limit of the certificate is not compared with the monetary limit of the signed document, the user should be warned that the signer certificate has a monetary limit and “VALID Signature” message must be displayed.